Fortigate Web Filtering Guide: Modes, Usage & Best Practices
When it comes to network security, Fortigate web filtering is one of the most powerful tools administrators can use to protect users from harmful, inappropriate, or non-business-related content. Whether you’re managing a corporate office, an educational institution, or a public network, configuring web filtering correctly can help prevent malware infections, enforce productivity policies, and safeguard user privacy.
This guide will walk you through the different Fortigate web filtering modes, explain how they work, and share best practices on when to use each mode.
Why Web Filtering Matters in Fortigate Firewalls
With cyber threats evolving rapidly, traditional antivirus solutions aren’t enough. Web filtering provides an extra layer of defense by controlling access to websites based on categories, reputation, or custom rules. It helps to:
- Block malicious domains (phishing, malware, botnets).
- Restrict non-work-related browsing (social media, gambling, streaming).
- Comply with regulations (HIPAA, CIPA, GDPR).
- Improve bandwidth utilization by limiting streaming or downloads.
In short, Fortigate web filtering is not just about blocking websites.It’s about managing risk and enforcing policy.
Fortigate Web Filtering Modes Explained
Fortigate offers multiple web filtering inspection modes. Choosing the right one depends on your network requirements, performance expectations, and security goals.
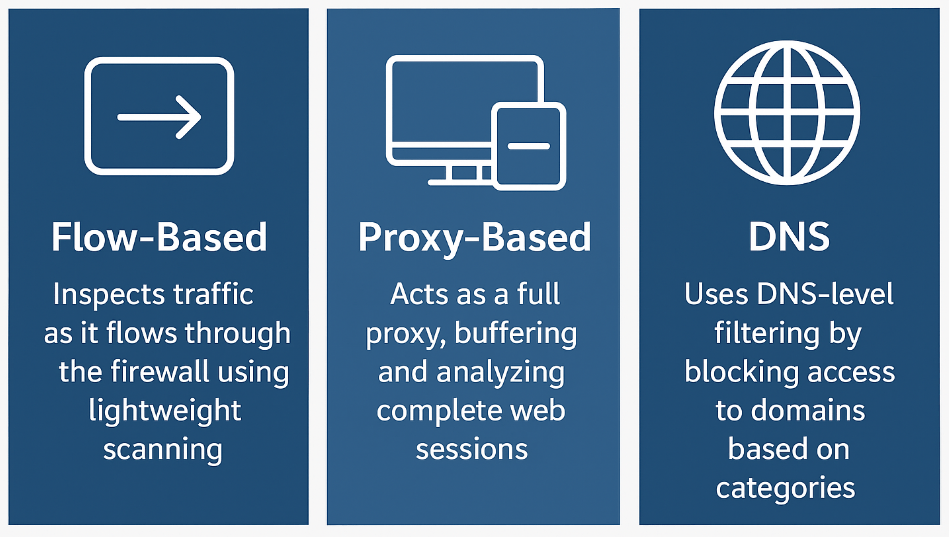
1. Flow-Based Web Filtering Mode
- How it works: Inspects traffic as it flows through the firewall using lightweight, high-speed scanning.
- Advantages: Faster performance, lower latency, and less resource-intensive.
- Best used when:
- Your primary focus is speed.
- You need basic URL filtering with minimal performance impact.
- Ideal for SMBs or high-throughput environments.
2. Proxy-Based Web Filtering Mode
- How it works: Acts as a full proxy, buffering and analyzing complete web sessions before forwarding them.
- Advantages: Provides deeper inspection and supports more advanced filtering options.
- Best used when:
- Security is more important than speed.
- You want detailed content inspection (e.g.. filtering keywords in search queries).
- You’re protecting sensitive environments such as finance or healthcare.
3. DNS Web Filtering Mode
- How it works: Uses DNS-level filtering by blocking access to domains based on categories or threat intelligence.
- Advantages: Extremely fast and lightweight, requires fewer resources, and works across all devices.
- Best used when:
- You need broad domain-level control.
- Protecting BYOD (Bring Your Own Device) environments.
- Complementing deeper inspection modes for layered security.
4. Hybrid Approach (Flow + DNS + Proxy)
Many organizations deploy a combination of modes to balance performance and security. For example:
- DNS filtering for broad domain control.
- Flow-based filtering for real-time scanning.
- Proxy-based filtering for sensitive departments (HR, Finance).
This layered strategy ensures you don’t sacrifice speed for security.
When to Use Each Web Filtering Mode
| Mode | Best For | When to Use |
|---|---|---|
| Flow-Based | High performance, minimal delay | Offices needing speed over deep inspection |
| Proxy-Based | Deep analysis, content control | Sensitive industries, compliance-heavy sectors |
| DNS Filtering | Lightweight domain blocking | Schools, BYOD networks, first defense layer |
| Hybrid | Balanced security & performance | Enterprises with diverse needs |
Best Practices for Fortigate Web Filtering
To get the most from Fortigate’s web filtering features, follow these practices:
- Start with DNS filtering for broad category-based protection.
- Use flow-based filtering on high-performance networks.
- Enable proxy-based filtering for departments handling sensitive data.
- Regularly update FortiGuard categories to ensure new threats are blocked.
- Create custom block/allow lists for specific business needs.
- Monitor logs and reports to fine-tune filtering policies.
FAQs: Fortigate Web Filtering Guide
1. What is the difference between flow-based and proxy-based filtering?
Flow-based is faster but less thorough, while proxy-based offers deeper inspection at the cost of speed.
2. Does DNS web filtering work without SSL inspection?
Yes, since it operates at the DNS level, it blocks domains before HTTPS connections are established.
3. Can I use multiple Fortigate filtering modes together?
Absolutely. Many administrators use DNS filtering as a first layer, with proxy or flow for deeper inspection.
4. How often should I update Fortigate’s web filter database?
Daily updates are recommended since new malicious domains appear constantly.
5. Does web filtering slow down internet speed?
Flow-based and DNS filtering have minimal impact, but proxy-based filtering may reduce performance slightly.
6. Is Fortigate web filtering suitable for schools?
Yes, especially with DNS filtering and category-based restrictions, it helps comply with CIPA regulations.
Fortigate web filtering is a powerful feature that provides administrators with flexible modes to balance performance and security. By understanding flow-based, proxy-based, and DNS filtering modes, you can choose the best configuration for your organization’s needs.
Implementing a hybrid strategy and following best practices will ensure your network stays secure, compliant, and productive.
Ready to strengthen your network security? Start by testing Fortigate’s DNS web filtering as your first line of defense!.
Recommended Resource: Fortinet Official Documentation – Web Filtering